Back to resources
Static Access Is Dead: Why Zero Standing Privileges Is Your Identity Security Superpower
July 2025 / 7 min. read /

Static access is a liability.
Credentials that remain active indefinitely, like admin passwords, hard-coded tokens, and access keys, pose a persistent and growing risk.
Whether it’s a forgotten service account in Jenkins, a dormant admin role in AWS, or an AI agent with unrestricted access to sensitive data, the story is the same: over-permissioned identities create silent vulnerabilities.
It’s time to move on from always-on access.
Enter: Zero Standing Privileges?
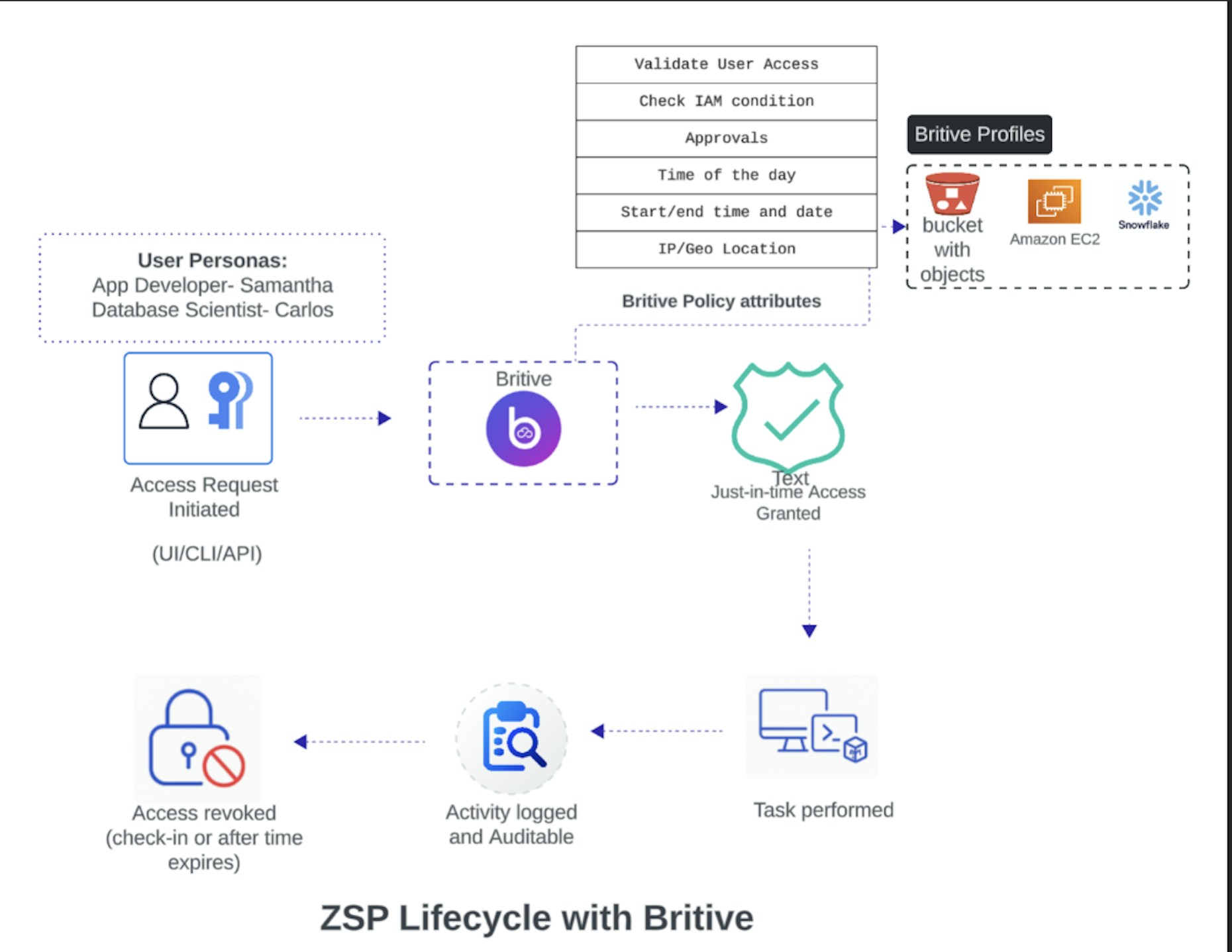
Zero Standing Privileges (ZSP) is a security model where no identity, human, machine, or AI, retains persistent access to critical systems or data. Access is provisioned dynamically, just-in-time (JIT), and revoked automatically when no longer needed.
ZSP flips the traditional "always-on" model on its head.
Instead of granting broad, indefinite permissions, it enforces just-enough access for just-long-enough. Nothing stands idle. Nothing is left behind.
This isn’t just a new flavor of privileged access management. It’s a shift in how access should work in modern environments.
Why Static Credentials Are a Crisis
Despite the rise of Zero Trust, many environments are still filled with static credentials. Why?
- Developers hard-code secrets into pipelines for speed.
- Admins create one-time fixes that never get cleaned up.
- AI agents and bots are granted sweeping roles for convenience.
The result?
- Thousands of unused or over-permissioned accounts across cloud environments.
- Credentials buried in config files or exposed in public repos.
- A sprawling, largely invisible access surface attackers love to exploit.
Most breaches don’t start with a zero-day. They start with a forgotten key.
ZSP vs. Traditional Just-in-Time Access
Not all JIT models are created equal.
Some tools vault credentials and "just-in-time" their exposure to users. But those accounts and permissions still exist permanently in your environment. If compromised, they remain dangerous.
ZSP goes further. It eliminates static access entirely. Privileges are generated and scoped per task, then automatically destroyed. There are no lingering secrets to steal, no dormant entitlements to abuse.
ZSP in Action: 3 Real-World Examples
1. Cloud App Developer Needs Temporary S3 Access
Samantha, a developer, needs admin rights to debug a pipeline. In a legacy setup, she might have persistent access to the entire AWS account.
With ZSP: Samantha requests time-limited access via CLI or API. The request is scoped according to her needs and approved. Access is granted and automatically revoked after the task is completed. Her actions are logged for auditability.
2. Data Scientist Requests Read-Only Snowflake Access
Carlos needs access to customer metrics for a weekly report. Historically, he might have used standing access to the entire Snowflake warehouse.
With ZSP: Carlos requests read-only access tied to his project. He gets access to view just the rows he needs for a set period of time, and nothing more. No residual access remains.
3. Agentic AI Automates DevOps Across Systems
A LangChain-based AI agent automates deployment: it pulls from GitHub, pushes to S3, and updates Snowflake dashboards. Without ZSP, this workflow would rely on static service accounts.
With ZSP: The agent triggers just-in-time access to each system. Permissions are granted based on dynamic policy, then revoked immediately. No secrets are stored and every action is logged for continuous visibility.
Real-World Benefits of ZSP
1. Ephemeral, Time-Bound Access
Access exists only when needed—then disappears. No lingering roles, no default keys.
2. Unified Governance for All Identities
Human, machine, and AI identities are managed under one policy model. No silos. No exceptions.
3. Automation-Friendly, Developer-Aligned
ZSP integrates with CI/CD pipelines, APIs, and developer workflows without blocking delivery.
4. Audit-Ready by Default
Every access request is logged, scoped, and traceable. Audits go from reactive to real-time.
The Future: Continuous, Behavior-Based Authorization
Zero Standing Privileges is the foundation. The next evolution is continuous access enforcement:
- Evaluate access not just at request time, but throughout the session.
- Detect anomalous behavior and revoke access in real time.
- Apply adaptive policies that respond to changing context.
Identity security platforms will function more like identity firewalls enforcing Zero Trust continuously, not just at the point of entry.
Operationalizing Zero Standing Privileges for the Modern Cloud
ZSP is a powerful concept but making it operational takes the right architecture.
Britive’s cloud-native platform is purpose-built to enforce Zero Standing Privileges across modern, multi-cloud environments.
- Eliminates always-on access with just-in-time provisioning and auto-expiration.
- Separates authentication from authorization: logging in doesn’t equal access.
- Delivers context-aware access control with dynamic, policy-based enforcement.
- Supports human + machine + AI identities with one unified policy model.
- Deploys quickly via API-first and proxy-less architecture.
- Provides full auditability & visibility into every access request and revocation.
Final Thoughts
Zero Standing Privileges isn’t just a security control: it’s a strategy for reducing risk, enabling speed, and simplifying governance at scale.
The future of identity security is ephemeral, contextual, and intelligent. ZSP is where it starts.
Britive helps teams operationalize this strategy across developers, pipelines, and AI agents with a platform that’s lightweight, scalable, and built for the cloud reality we live in. Ready to dive in and learn more? Contact a member of our team to get a customized demo.


